Prerequisites
- Ensure that you have a Vantage tenant identifier before configuring identities. To get a tenant identifier, by click Configuration in ABBYY Vantage. The identifier is on the General tab.
- Create a Redirect URI to receive the authentication responses. The URI is:
https://<your-vantage-url>/auth2/Saml2/Acs
Setup
The setup process consists of the following steps:- Adding claim description
- Configuring relying party trust
- Adding rules to transform an incoming claim
Adding a Claim Description
- Open the management console.
- Select Service > Claim Descriptions. Click Add Claim Description.
- Fill in the required fields:
- Specify a display name: such as Persistent Identifier.
- Specify a claim type:
urn:oasis:names:tc:SAML:2.0:nameid-format:persistent. - Select Publish this claim description in federation metadata as a claim type that this federation service can accept.
- Select Publish this claim description in federation metadata as a claim type that this federation service can send.
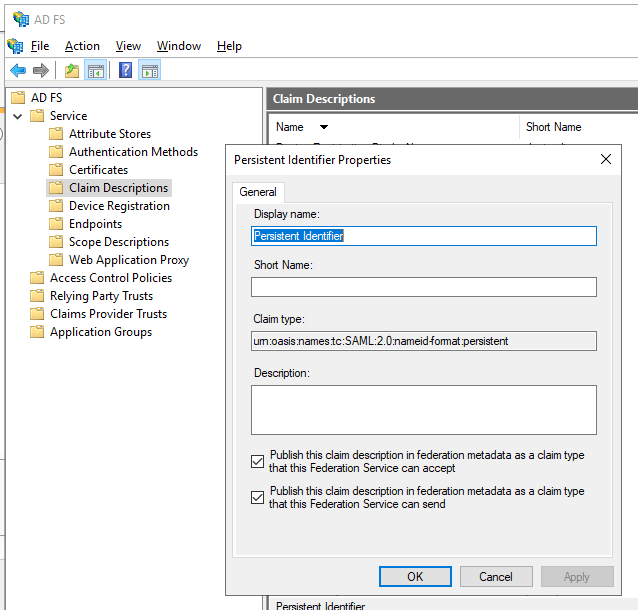
- Click OK.
Configuring a Relying Party Trust
To create an ADFS relying party trust, follow these steps:- In the console tree, under AD FS, select Trust Relationships > Relying Party Trusts > Add Relying Party Trust.
- On the Welcome page, choose Claims aware and select Start.
- On the Select Data Source page, select Enter data about the relying party manually, and then select Next.
- On the Specify Display Name page, enter any name in Display Name, and then select Next.
- On the Choose Profile page, select the ADFS 2.0 profile, and then click Next.
- On the Configure Certificate page, click Next.
- On the Configure URL page, select the Enable support for the SAML 2.0 WebSSO protocol. Under Relying party SAML 2.0 SSO service URL, enter
https://<your-vantage-url>/auth2/Saml2/Acs, and then click Next. - To configure identities, follow these steps:
- Under Relying party trust identifier, enter
api://platform.abbyy.cloud/tenantId, where tenantId is the tenant identifier in GUID format without hyphens (for example, 117489fc1aea41658369d4d18d6557ga) This value will be used as the Application ID URI for authentication. Copy this value as you will need it when configuring the External Identity Provider in Vantage. Click Add. - In the Expose an API tab, set the Application ID URI to the same value you entered above (for example,
api://a37892f6-c2e9-4092-b804-d054741da4da). Click Add, and then click Next.
- Under Relying party trust identifier, enter
- If you want to provide access to Vantage to all users, select Permit all users to access this relying party in the Choose Issuance Authorization Rules window. Alternatively, select Permit specific group and specify the desired group if you want to provide access only to that specific group. Click Next.
- On the Ready to Add Trust page, review the settings. Click Next, and then click Close.
Adding Rules to Transform an Incoming Claim
To apply rules to transform an incoming claim, follow these steps:- Click Relying Party Trusts.
- Right-click the selected trust, and then click Edit Claim Issuance Policy.
- In the
Edit Claim Issuance Policy for <name>window that opens, click Add Rule.
- Select the Transform an Incoming Claim claim rule template, and then click Next.
- Select the Configure Claim Rule step, and then specify the following:
- In Claim rule name, specify TransformWindows account name.
- In Incoming claim type, select Windows account name.
- In Outgoing claim type, select Name ID.
- In Outgoing name ID format, select Persistent Identifier.
- Select Pass through all claim values.
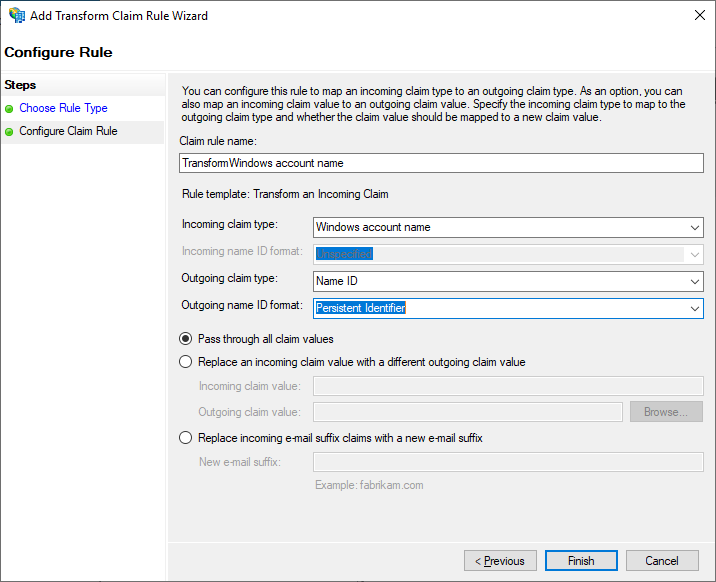
- Click Finish.
- Add another rule to ensure that e-mail and name claims are included in the issued token. On the Select Rule Template page, select Send LDAP Attributes as Claims under Claim rule template, and then click Next.
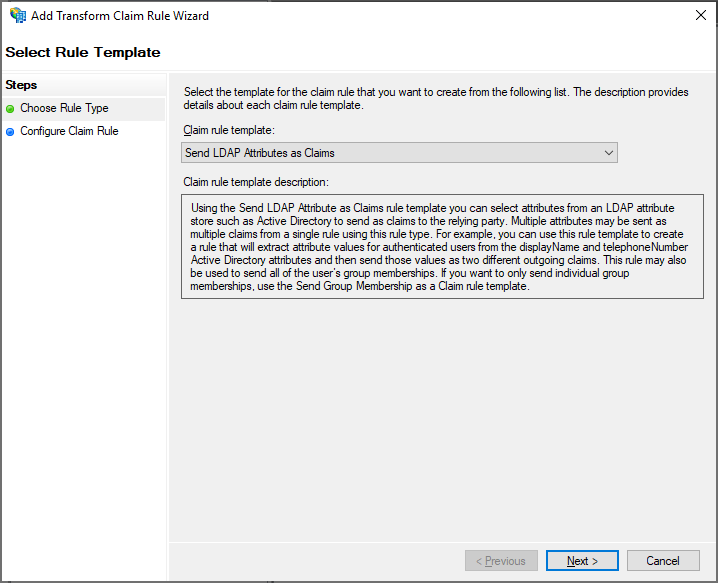
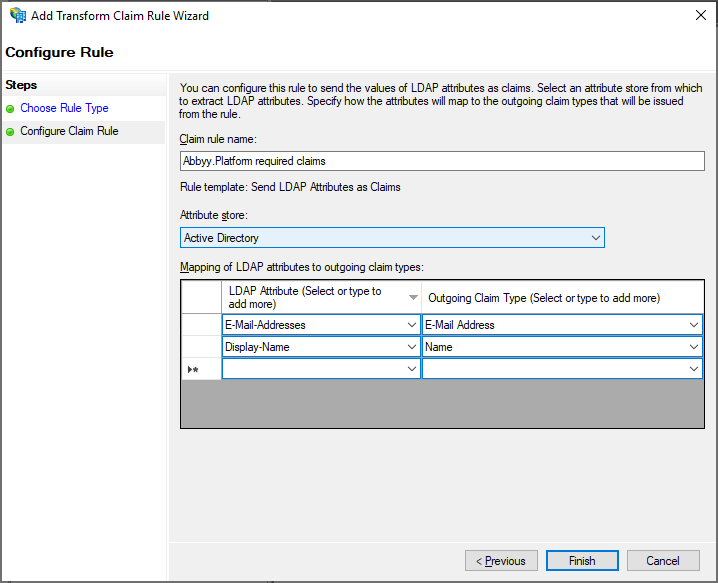
- On the Configure Claim Rule page, select the Active Directory attribute store under Claim rule name, and then click Finish.
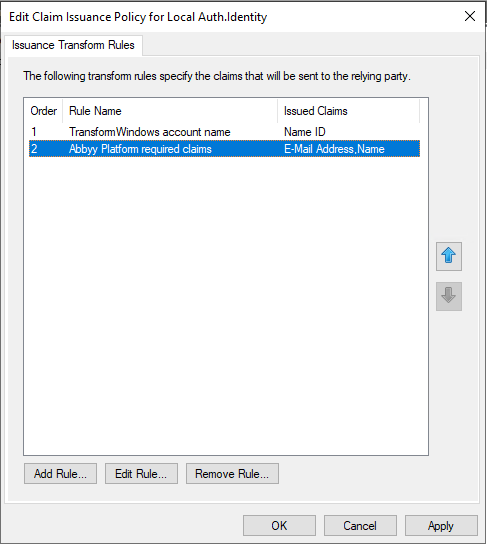
- The added rules are displayed in the Edit Claim Rules dialog box.
Next Steps
Set up authentication via a SAML 2.0 External Identity Provider for your tenant in Vantage, which requires the federation metadata document URL in the following format:https://<adfs_server_address>/federationmetadata/2007-06/federationmetadata.xml. For example, https://adfs.platform.local/federationmetadata/2007-06/federationmetadata.xml.
For more information, see Setting up an External Identity Provider for a tenant.